
Road Network Operations
& Intelligent Transport Systems
A guide for practitioners!

Road Network Operations
& Intelligent Transport Systems
A guide for practitioners!
The application of a security-minded approach requires road operators, working with partner organisations and security advisers, to understand potential threats and their impact, identify key vulnerabilities and analyse the nature of measures required to manage risks. (See Planning and Reporting) The goal is to enhance the safety, security and resilience of the road network and its associated infrastructure.
Three key elements in the risk management process are:
A road authority, with its partner organisations and advisers, should develop a risk management strategy that incorporates each of these three elements – such as the one in the example outlined below.
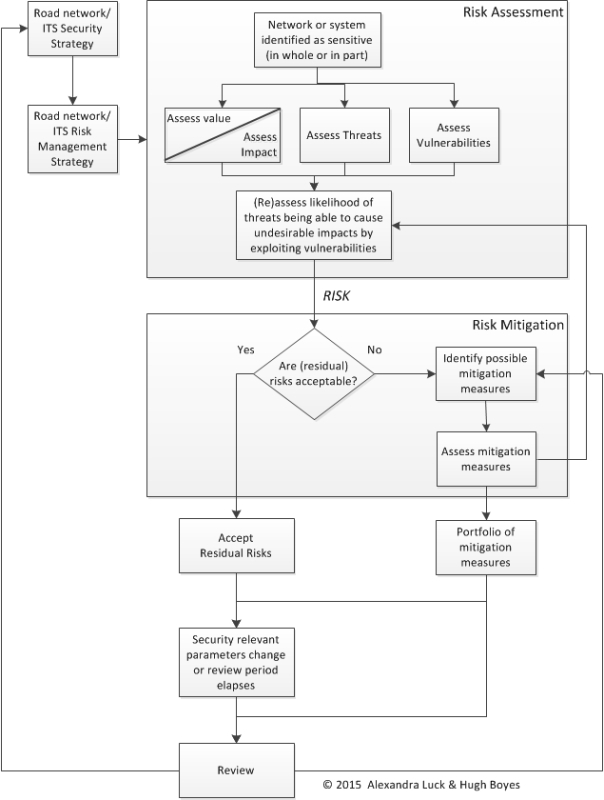
A systematic approach is useful in developing a risk management strategy – for which a checklist of questions is helpful to guide practitioners through the evaluation process:
A risk assessment should consider the potential threats to regular road use and operations and consequential vulnerabilities. Some threats that compromise network resilience are quite common, others are less frequent or rare. (See Security Threats) An essential part of the assessment is to consider how likely it is that a particular threat might happen and how disruptive it would be. The assessment needs to consider what harm might be caused to:
A vulnerability in the context of road network security is defined as a weakness in the road infrastructure or operating systems that can be exploited by one or more threats.
Vulnerabilities associated with the construction, operation or maintenance of the road network relate to its scale, and how easy it is to:
Vulnerabilities that affect highway network operations concern cabling, equipment, sensors and associated processing systems that might be attacked:
The likelihood of threats may be relatively predictable for environmental, social, economic or political reasons. For example, a project’s level of profile, its controversy and its impact on local communities will influence how likely it is to provoke civil protests and strikes, malicious attacks, or theft of equipment such as construction plant.
The likelihood of a threat being realised will be greater if security is poor, for example when:
In order to maintain the security of the road network and supporting systems it is necessary to establish a process whereby:
Report of the PIARC Security Task Force (See Security of Road Infrastructure)