

The road network and vehicle industry are at the beginning of a period of significant change as innovative solutions are sought to improve the safety, serviceability, sustainability and resilience of infrastructure. The way in which networks are managed and the way in which road space is utilised is evolving – with greater use of technology to monitor network conditions and to actively manage traffic. (See ITS and Network Monitoring and Traffic Management) There has also been a significant increase in the complexity of vehicle technology – for example, the use of hybrid and electric vehicles, and developments relating to vehicle connectivity and automation. (See Driver Support)
Changes in the use of technology create vulnerabilities. These are open to exploitation for malicious or hostile reasons – risking interference with vehicles and infrastructure. A security minded approach is necessary to assess and minimise potential risks and to manage incidents and evaluate measures taken.
A security-minded approach is defined as the understanding of the need for – and routine application of – appropriate and proportionate security measures to deter and/or disrupt hostile, malicious, fraudulent and criminal behaviours or activities. This approach needs to address four areas – people, processes, physical security and technical security.
By integrating these four areas it is possible to create an approach to network security that delivers:
The application of a security-minded approach requires road operators to work with partner organisations, such as the police, and security advisers. (See Planning and Reporting) This helps to develop an understanding of potential threats and their impact, key vulnerabilities and the nature of mitigating measures required. A failure of security – for any reason – will require a full assessment so that the reasons for failure are understood and lessons can be learnt. (See Emergency Response)
The application of a security-minded approach requires road operators, working with partner organisations and security advisers, to understand potential threats and their impact, identify key vulnerabilities and analyse the nature of measures required to manage risks. (See Planning and Reporting) The goal is to enhance the safety, security and resilience of the road network and its associated infrastructure.
Three key elements in the risk management process are:
A road authority, with its partner organisations and advisers, should develop a risk management strategy that incorporates each of these three elements – such as the one in the example outlined below.
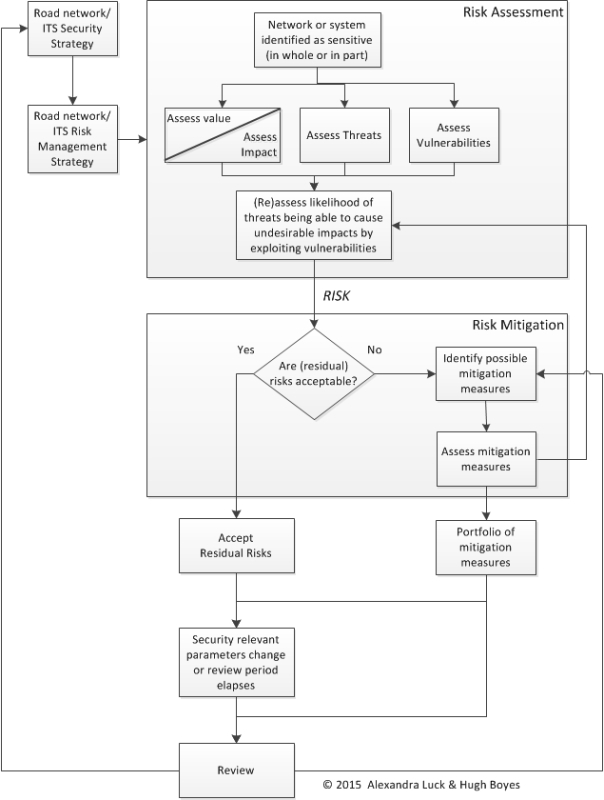
Road infrastructure security risk management strategy
A systematic approach is useful in developing a risk management strategy – for which a checklist of questions is helpful to guide practitioners through the evaluation process:
A risk assessment should consider the potential threats to regular road use and operations and consequential vulnerabilities. Some threats that compromise network resilience are quite common, others are less frequent or rare. (See Security Threats) An essential part of the assessment is to consider how likely it is that a particular threat might happen and how disruptive it would be. The assessment needs to consider what harm might be caused to:
A vulnerability in the context of road network security is defined as a weakness in the road infrastructure or operating systems that can be exploited by one or more threats.
Vulnerabilities associated with the construction, operation or maintenance of the road network relate to its scale, and how easy it is to:
Vulnerabilities that affect highway network operations concern cabling, equipment, sensors and associated processing systems that might be attacked:
The likelihood of threats may be relatively predictable for environmental, social, economic or political reasons. For example, a project’s level of profile, its controversy and its impact on local communities will influence how likely it is to provoke civil protests and strikes, malicious attacks, or theft of equipment such as construction plant.
The likelihood of a threat being realised will be greater if security is poor, for example when:
In order to maintain the security of the road network and supporting systems it is necessary to establish a process whereby:
Report of the PIARC Security Task Force (See Security of Road Infrastructure)
Security threats can be divided into those which:
Threats can also be unintentional, non-directed or unpredicted – for example:
The potential level of impact will depend on the criticality of the asset, system or information affected. An example is shown in the photo below.

Road Interrupted by direct action (Source : PIARC Security Task Force)
Damage or disruption to the construction, operation or maintenance of the road infrastructure may arise from a number of threats.
Damage or disruption to the ITS infrastructure, operating systems and associated information may arise from:
A malicious attack can occur through a range of external and internal/insider threats. For example, damage may be caused by malware, hackers or disaffected personnel. Physical damage may be caused to:
Theft of IT equipment, sensors or cables within the highway boundary can lead to loss of functionality or system resilience. It can also impact on the ability of the infrastructure system to perform as efficiently as it would otherwise. Repair and replacement can be disruptive and problematic.
Counter-measures can help reduce the level of threat to the security of roads and highways and mitigate the potential for disruption. The decision whether to accept identified risks or implement mitigation measures, (and what measures to deploy) may fall to different parties according to the circumstances. It may be:
The decision about what mitigation measures will be implemented will depend on a number of factors:
Damage or disruption to the construction, operation or maintenance of the highway network arising from intended events – such as civil protests and strikes, malicious attacks, or theft of equipment – may be managed by improving security. For example:
Measures relating to the design, location and physical security of equipment cabinets, sensors and cabling routes – which may be at risk from theft or other malicious attack – should be taken into consideration when the assets are first introduced. For existing assets, physical security measures will need to be proportionate – when balancing cost and constraints against the impact of the loss, compromise or failure of the network and associated assets.
A security minded approach can manage the risk of loss, theft or corruption of software systems, systems for processing financial and/or personal data, and systems providing communications or power supply. This approach is based on the implementation of appropriate and proportionate policies, processes and procedures focusing on four areas – people, business process, physical security, and cyber-security. (See Network Security)
Where wireless technologies are employed in the system, consideration needs to be given to the impact of jamming or interference, and appropriate measures adopted to protect system confidentiality, integrity and availability. Depending on the criticality of individual systems, a variety of business continuity and disaster recovery solutions may also need to be developed.
ITS makes use of technologies such as Bluetooth, mobile phones and licence plate recognition to monitor traffic behaviour, improve traffic flows and road safety. Many of these systems – such as CCTV, video image processing and vehicle licence plate recognition – can sometimes be used specifically for security purposes. (See CCTV)
ITS is also extensively used in emergency situations to support crisis management and enforcement purposes. (See Emergency Response and Policing / Enforcement) These systems have to be robust enough to withstand unintentional, non-directed and unpredicted events.
The latest ITS applications, use connected vehicle technology to offer added-value services and safety support to the driving public. The possibility, though, that they may malfunction – or be subject to cyber-attack – needs to be taken into account by system designers and operator. (See Connected Vehicles)
In order to manage the security risks around greater automation and connectivity, it is vital that security of the whole system is considered. Alongside the security safeguards that are built into road vehicles it is important that the security of traffic management systems is also addressed.
With the current levels of automation in vehicles being very low, security breaches of existing traffic management systems are the most likely risk to efficient operations and increased congestion. Any such breach would bring with it a risk of reputational damage to the relevant highway authority or operating company. It may also impact on the safety of road users if the ability to detect and verify incidents is impeded. This is particularly the case during the hours of darkness when a stationary vehicle on the roadway can be difficult for drivers to detect, and when traffic speeds are high.
If control rooms become more automated in the future, the tolerance of risk will need to decrease as the need for assurance around the security of the systems becomes greater. Mitigation measures will need to be reviewed to ensure that the level of residual risk is at an acceptable level and does not exceed the level that can be tolerated by the road operator – or by road users in general.
Security risks will need to be comprehensively reassessed with the introduction of Vehicle-to-Infrastructure (V2I) communications into traffic management systems. This is especially so when V2I is used in combination with Vehicle-to-Vehicle (V2V) systems and greater vehicle autonomy. There will need to be far greater emphasis on safety and the prevention of incidents, particularly those that could cause injury or loss of life. For example, V2I systems that regulate vehicle speed or lane use may be vulnerable to streaming of incorrect or malicious data from insecure sources (vehicles) or other attacks on the system infrastructure. This could put large numbers of vehicles and their occupants at risk.
At levels three and four the automation will probably begin to include both V2V and V2I connectivity – to support increasingly automated driving and navigation processes.
As a result of the relatively long life of vehicles compared to the rapid development and deployment of new technologies, there will be a mixed fleet of vehicles using the highway at any one time. This may range from those with the very latest communications and automation features, to those which are older with legacy systems. The road network and its associated infrastructure will need to be able to ensure the safe interaction of vehicles with these varying capabilities.
Increasing automation – ultimately up to a level where a driver (like a passenger) has no control of the vehicle – raises legal questions surrounding:
To implement a security-minded approach for ITS, it is essential that security risks are understood not only during design stage, but throughout the lifecycle of operations. This requires the development of an ITS Security Strategy that sets out:
Alongside a risk management strategy for the network (See Security Planning), an ITS Security Management Plan is needed to detail the policies, processes and procedures needed to maintain the required level of security with clear roles and responsibilities for the road authority, the road operator, and any other parties that are directly involved in network operations. This should be embedded in other operating policies and reviewed regularly. (See Planning and Reporting)
The policies, process and procedures in the ITS Security Management Plan will need to deliver:
The immediate response to any incident or breach of security which impacts on the integrity of the road network, its associated assets and systems, and/or information is more likely to be effective if:
A security response plan increases the chance that local communities, businesses, transportation and emergency services will be able to continue to function following less severe incidents – without the need for the authorities to implement contingency arrangements. Where contingency arrangements become necessary, these should include business continuity measures as well as disaster and incident recovery actions. The aim is to mitigate impacts arising in the event of failure or impairment or non-availability of part of the network or related systems. (See Incident Response Plans)
To produce a plan of this type, it is necessary to identify:
In the event of a security incident, it is important that steps are taken to contain and recover from the event. (See Traffic Incidents)
During a security incident the response should include:
It may also be necessary to notify third parties – for example, service providers, regulatory bodies, and law enforcement agencies – in order to manage the incident effectively, including management of traffic on the surrounding network, and to minimise further disruption.
The provision of appropriate and timely information and advice to members of the public will also help in the management of the incident and minimise further disruption to the network. (See Emergency Response)